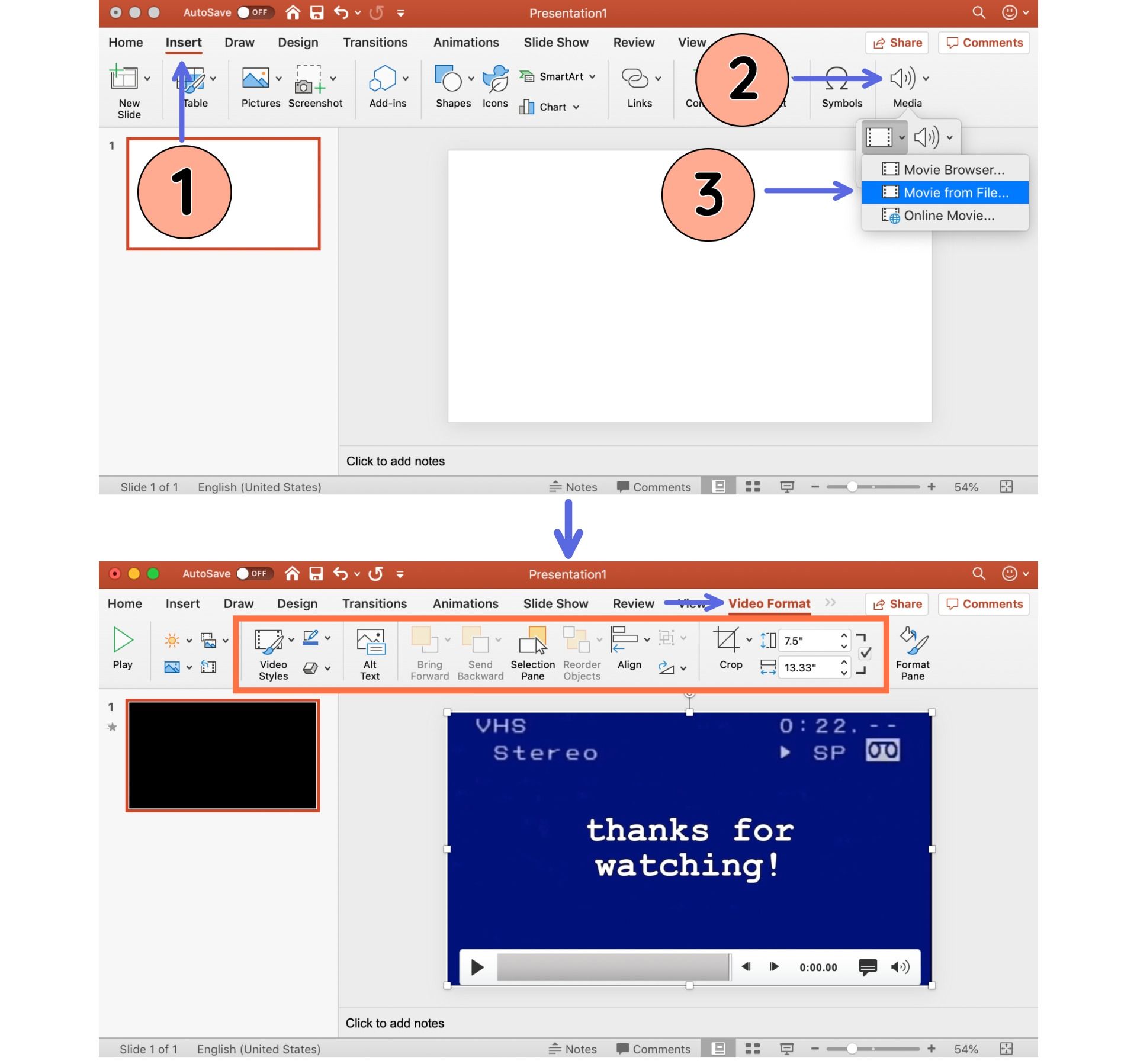
How To Insert Video In A Powerpoint Presentation
How To Insert Video In A Powerpoint Presentation - When the rewritten url is clicked in the email message, the web browser queries the risk level of the url from the web reputation services, which then takes the action. Trend micro analyzes those urls at the time of click, and will block access to them or show a warning page (depending on your settings) if they are malicious. At some point, the url may become too long and may not work anymore. There are no malicious signatures, click here to show all signatures. There are no malicious signatures, click here to show all signatures. Select a url rewrite settings. There are no malicious signatures, click here to show all signatures. A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a system and conduct malicious activities, such as stealing data and modifying. You can choose to use the. Select a url rewrite settings. A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a system and conduct malicious activities, such as stealing data and modifying. When the rewritten url is clicked in the email message, the web browser queries the risk level of the url from the web reputation services, which then takes the. A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a system and conduct malicious activities, such as stealing data and modifying. There are no malicious signatures, click here to show all signatures. When the rewritten url is clicked in the email message, the web browser queries the risk level of the url from the web. There are no malicious signatures, click here to show all signatures. At some point, the url may become too long and may not work anymore. When the rewritten url is clicked in the email message, the web browser queries the risk level of the url from the web reputation services, which then takes the action. There are no malicious signatures,. Trend micro analyzes those urls at the time of click, and will block access to them or show a warning page (depending on your settings) if they are malicious. A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a system and conduct malicious activities, such as stealing data and modifying. At some point, the url. There are no malicious signatures, click here to show all signatures. When the rewritten url is clicked in the email message, the web browser queries the risk level of the url from the web reputation services, which then takes the action. You can choose to use the. A backdoor is a type of cybersecurity threat that allows attackers to secretly. There are no malicious signatures, click here to show all signatures. A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a system and conduct malicious activities, such as stealing data and modifying. At some point, the url may become too long and may not work anymore. There are no malicious signatures, click here to show. There are no malicious signatures, click here to show all signatures. You can choose to use the. At some point, the url may become too long and may not work anymore. There are no malicious signatures, click here to show all signatures. Trend micro analyzes those urls at the time of click, and will block access to them or show. Select a url rewrite settings. There are no malicious signatures, click here to show all signatures. You can choose to use the. At some point, the url may become too long and may not work anymore. When the rewritten url is clicked in the email message, the web browser queries the risk level of the url from the web reputation. Trend micro analyzes those urls at the time of click, and will block access to them or show a warning page (depending on your settings) if they are malicious. When the rewritten url is clicked in the email message, the web browser queries the risk level of the url from the web reputation services, which then takes the action. A. There are no malicious signatures, click here to show all signatures. Trend micro analyzes those urls at the time of click, and will block access to them or show a warning page (depending on your settings) if they are malicious. Select a url rewrite settings. A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a.How to Insert Video into PowerPoint
How To Insert Slide Zoom In PowerPoint
How To Insert Files In Powerpoint Slide at Steven Schenk blog
How To Insert Slide Number And Footer In Powerpoint at Lucile Hart blog
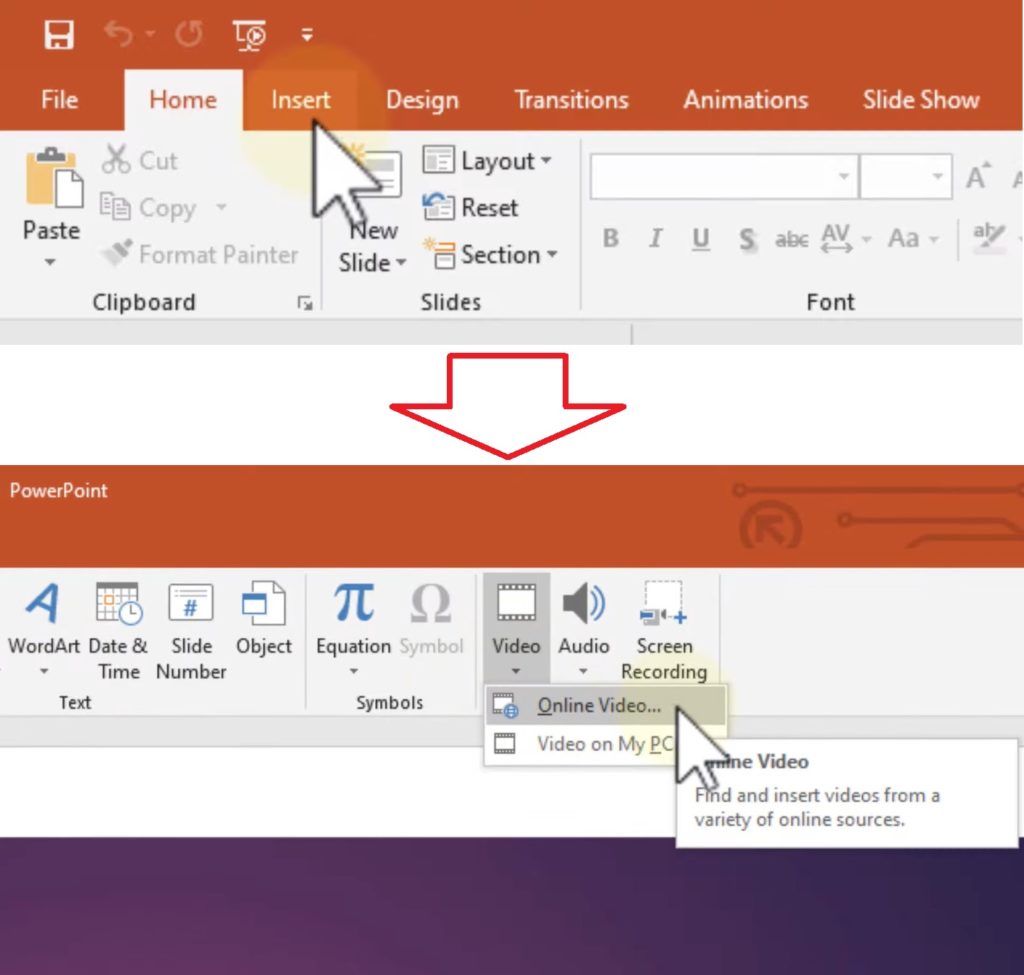
How to Embed Video in PowerPoint Quickly and Easily
Can You Insert A Slideshow Into Powerpoint at Marcia McCann blog
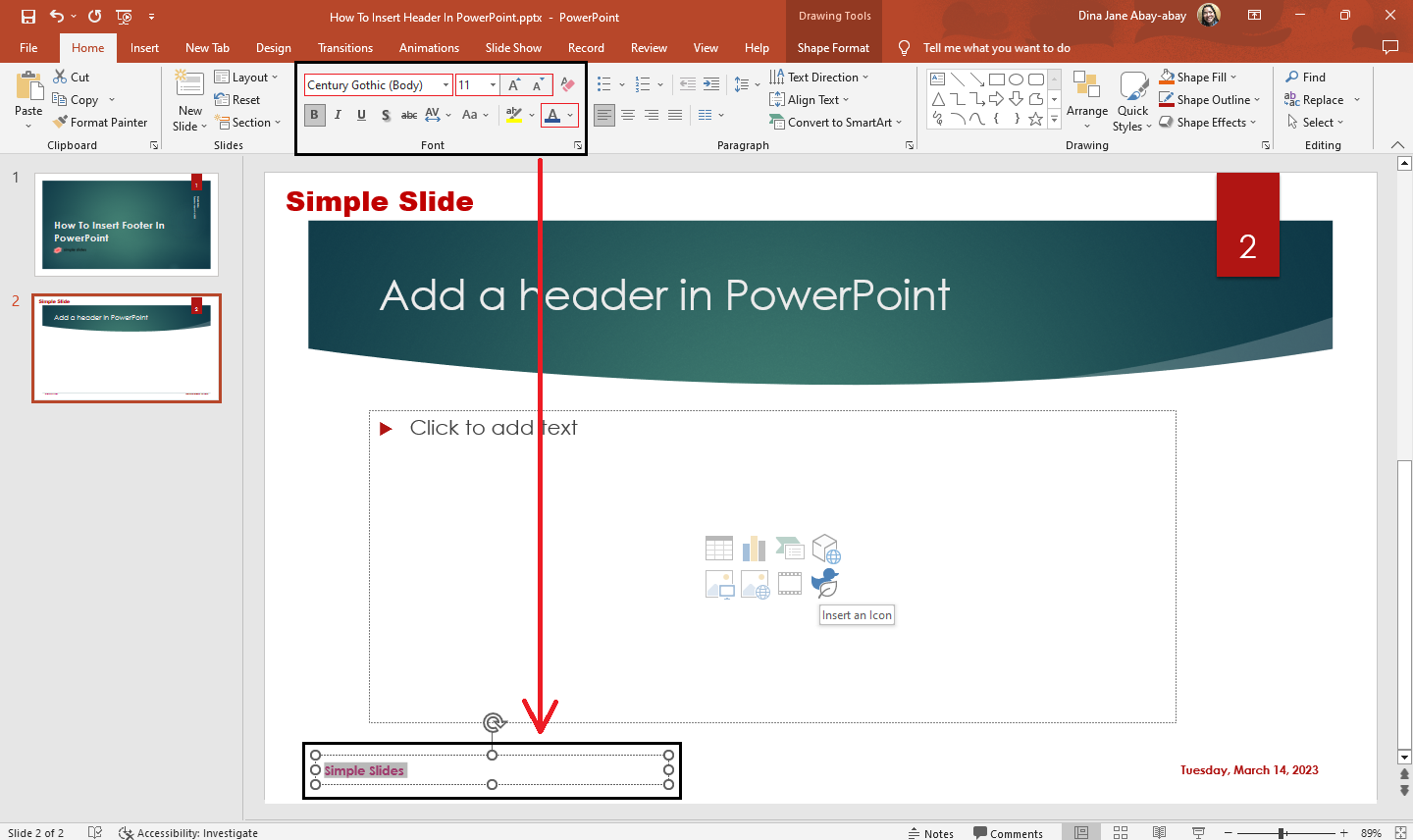
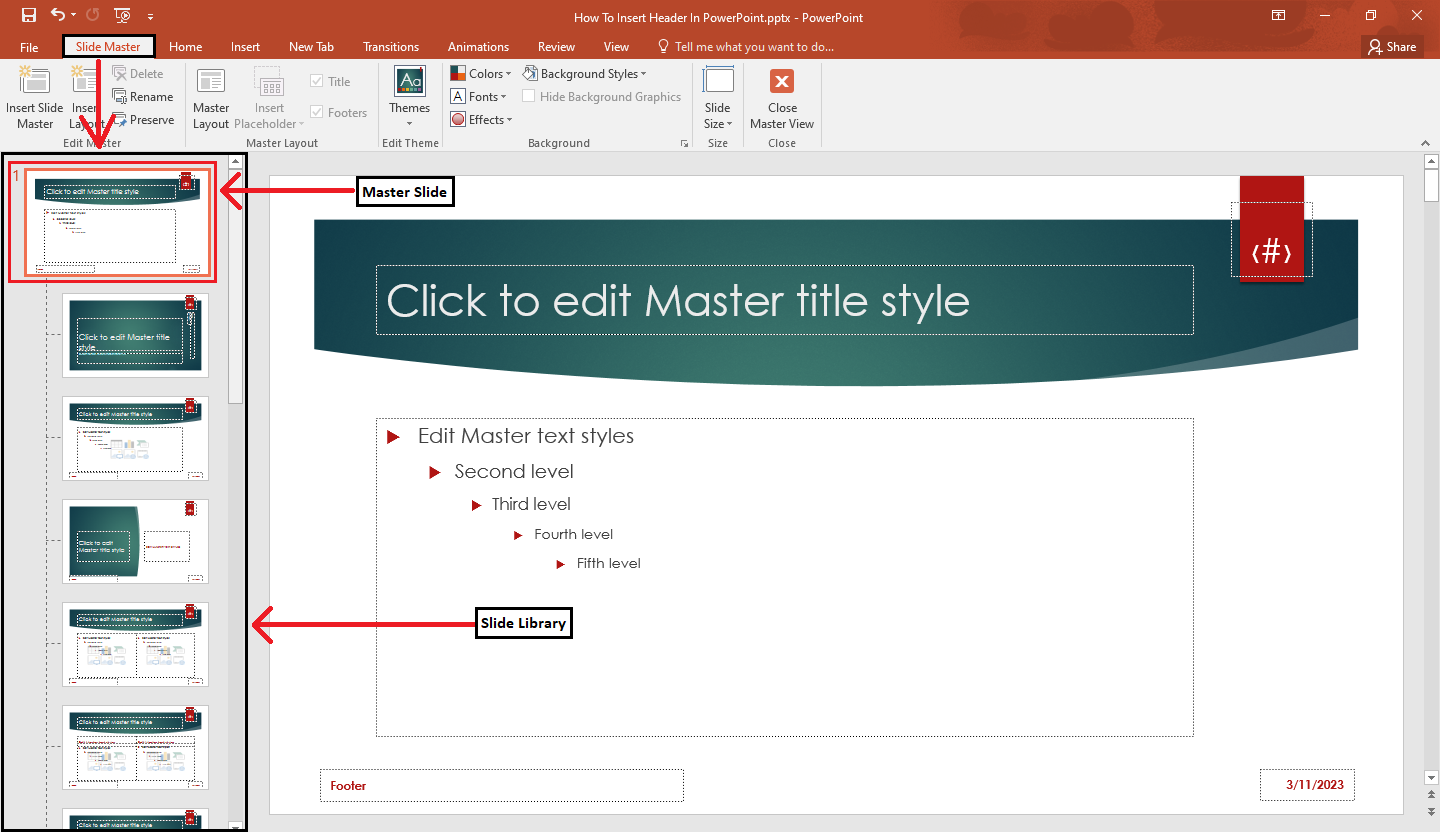
Learn How To Insert Header In PowerPoint
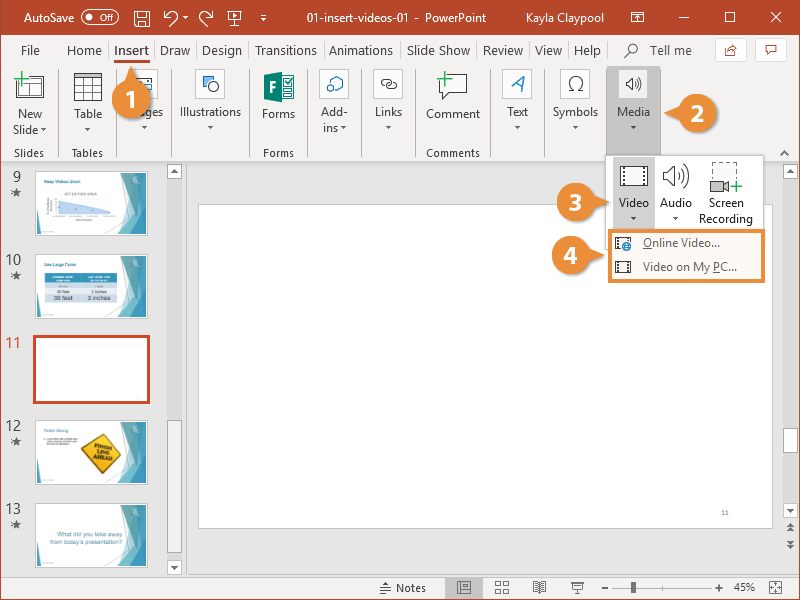
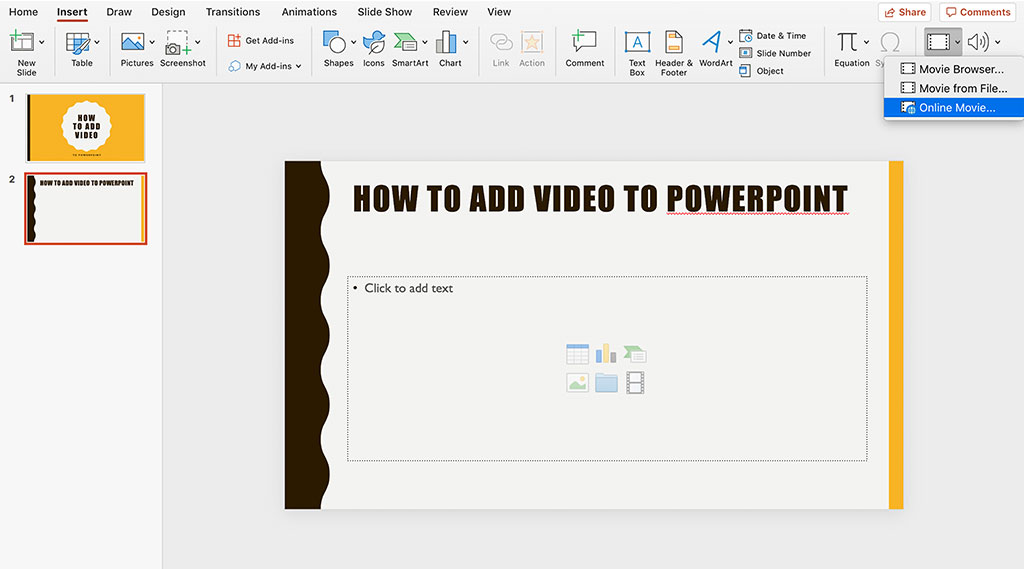
Quick Guide How to Add Video to PowerPoint Presentations
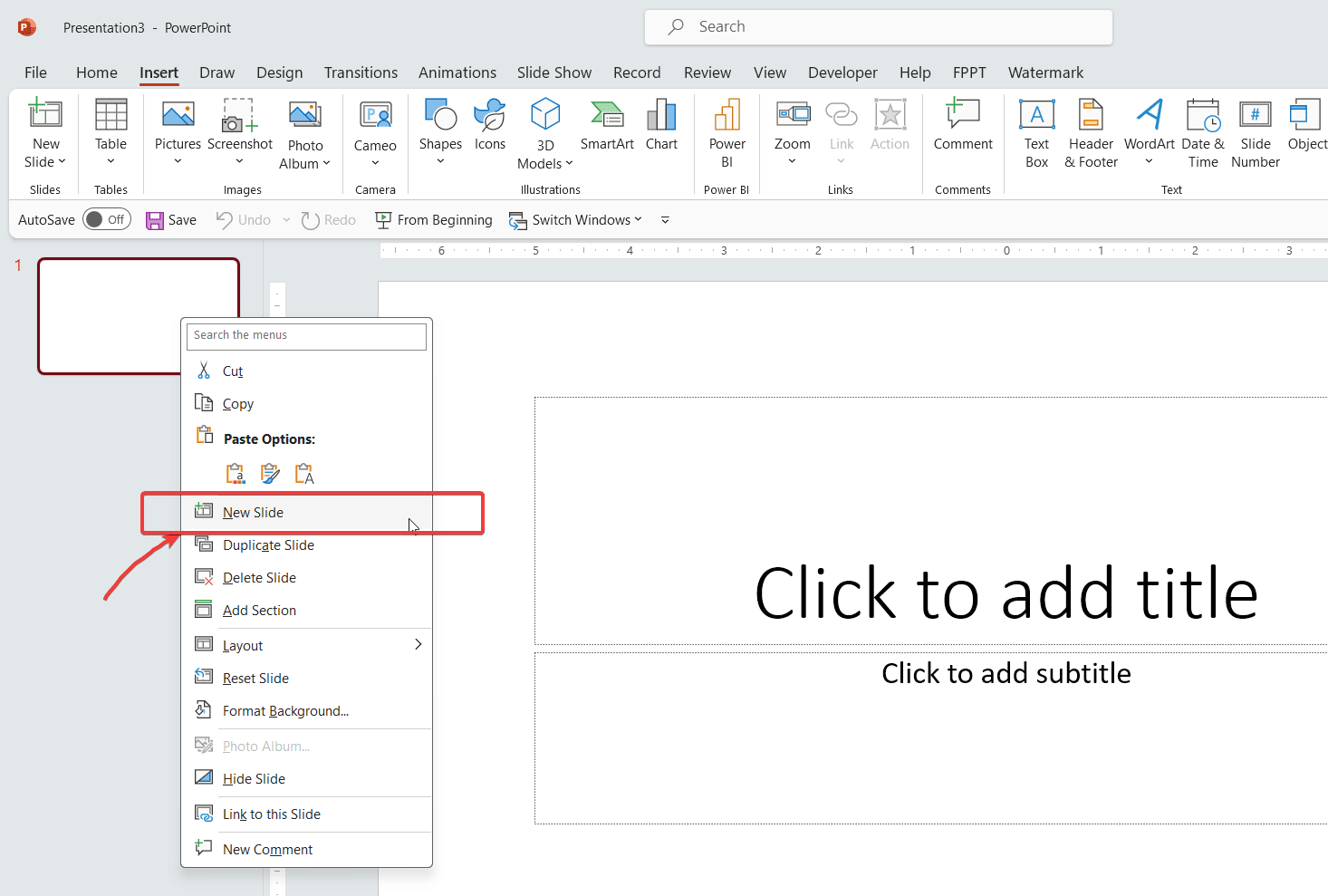
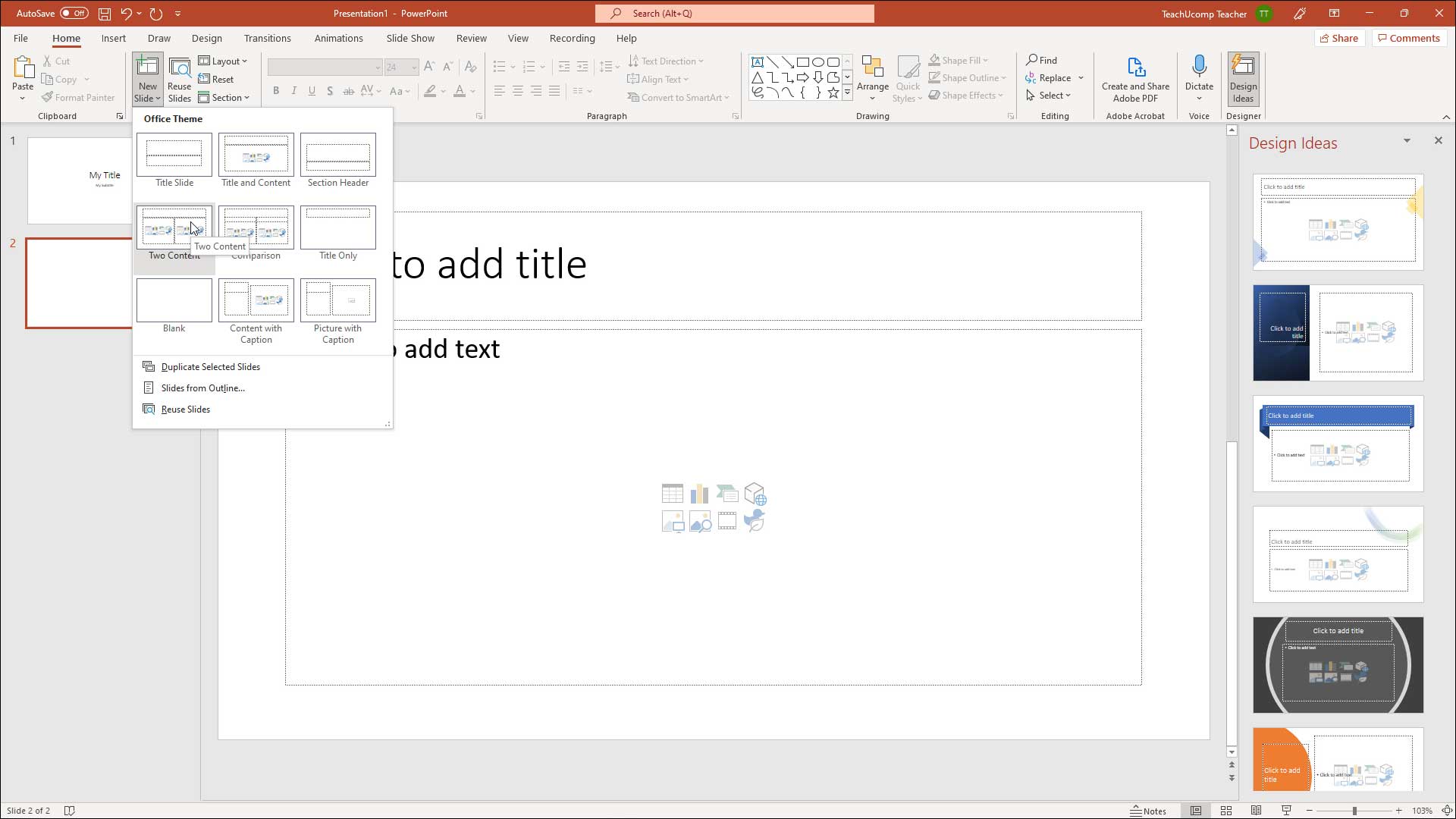
How to Add a Slide to a PowerPoint Presentation
How To Insert A Slide In A Powerpoint at Cheryl Talley blog
Related Post: