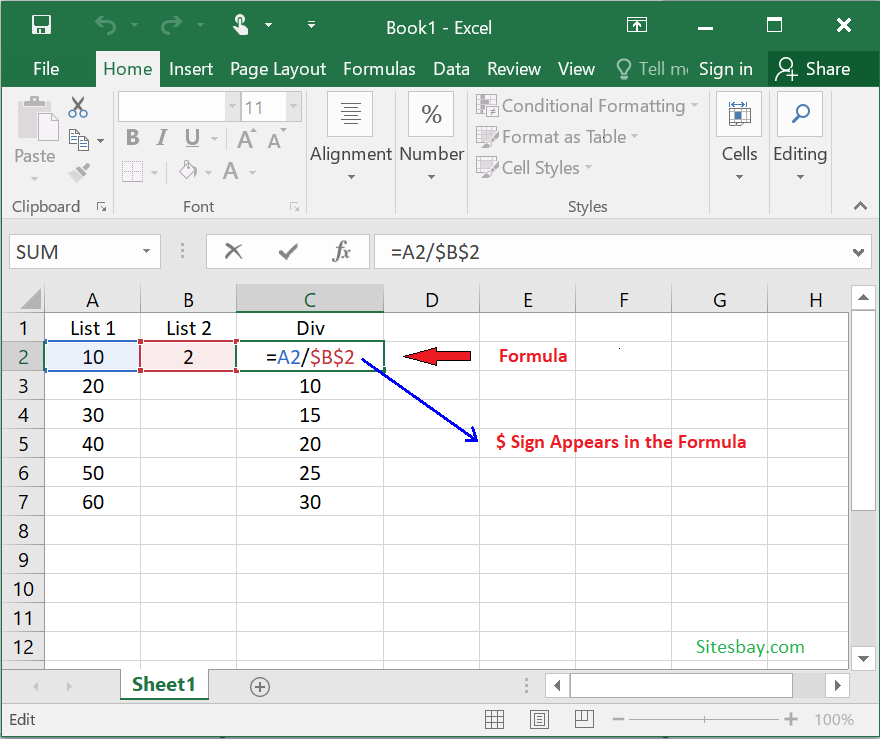
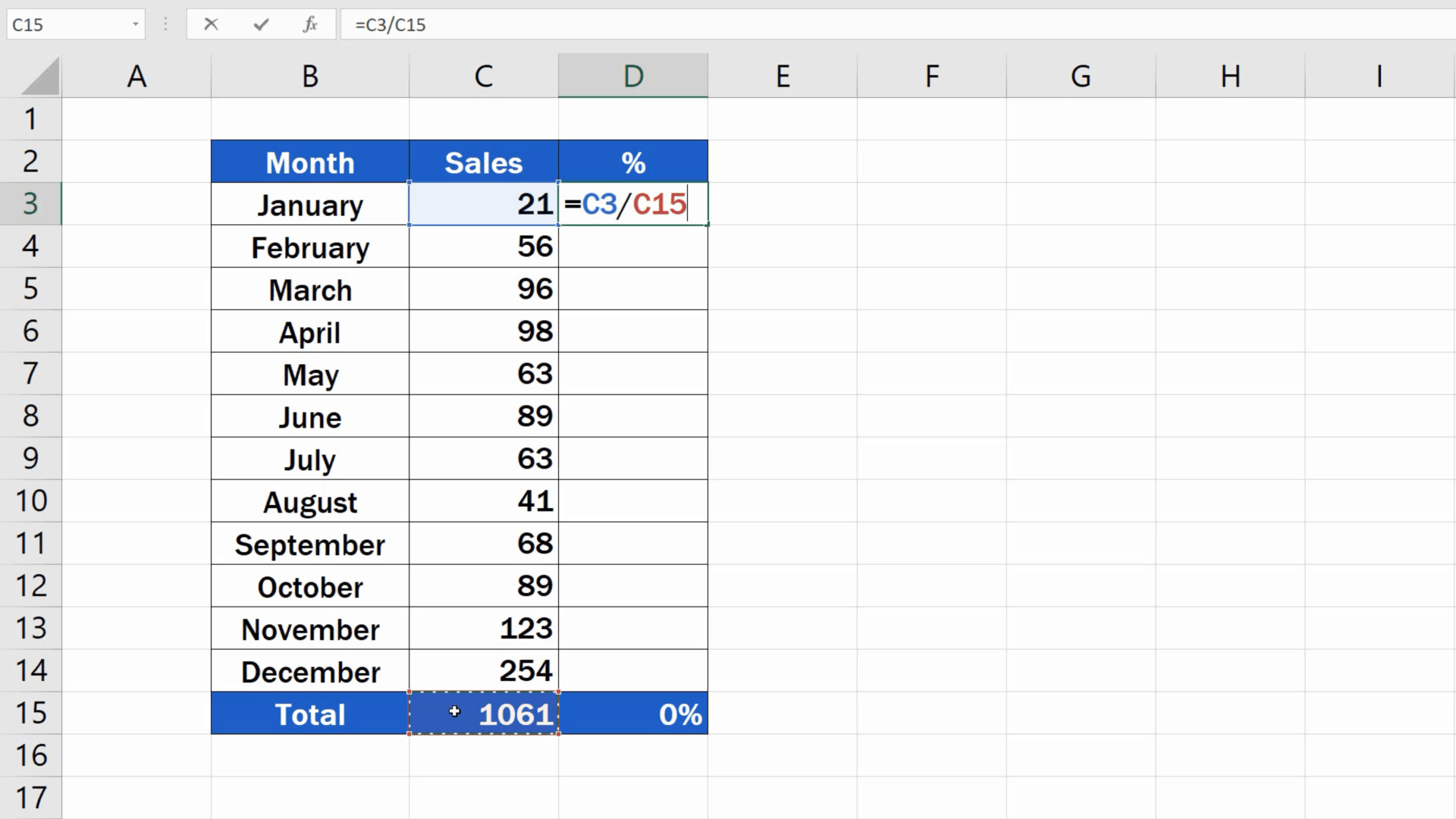
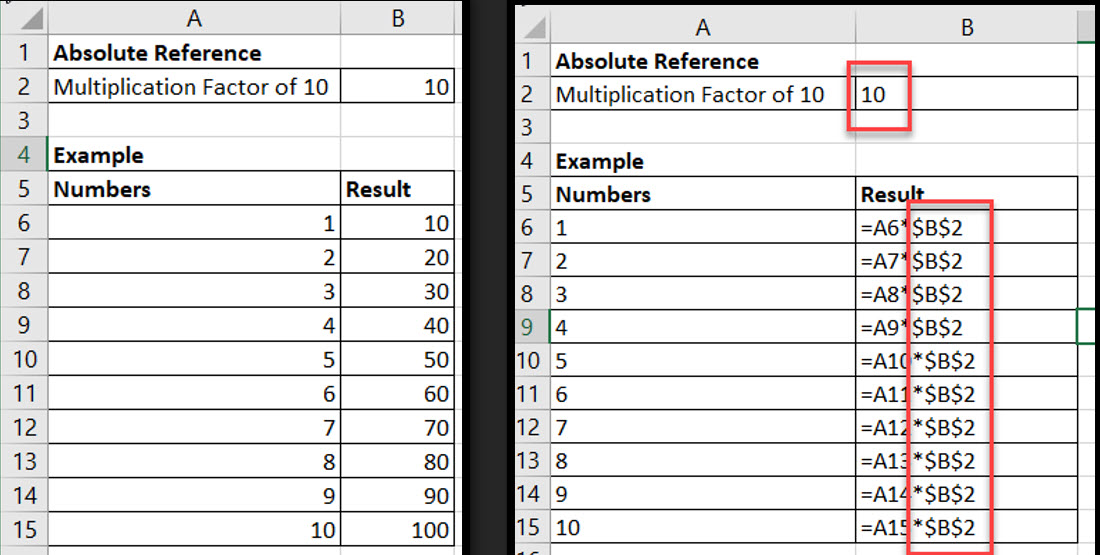
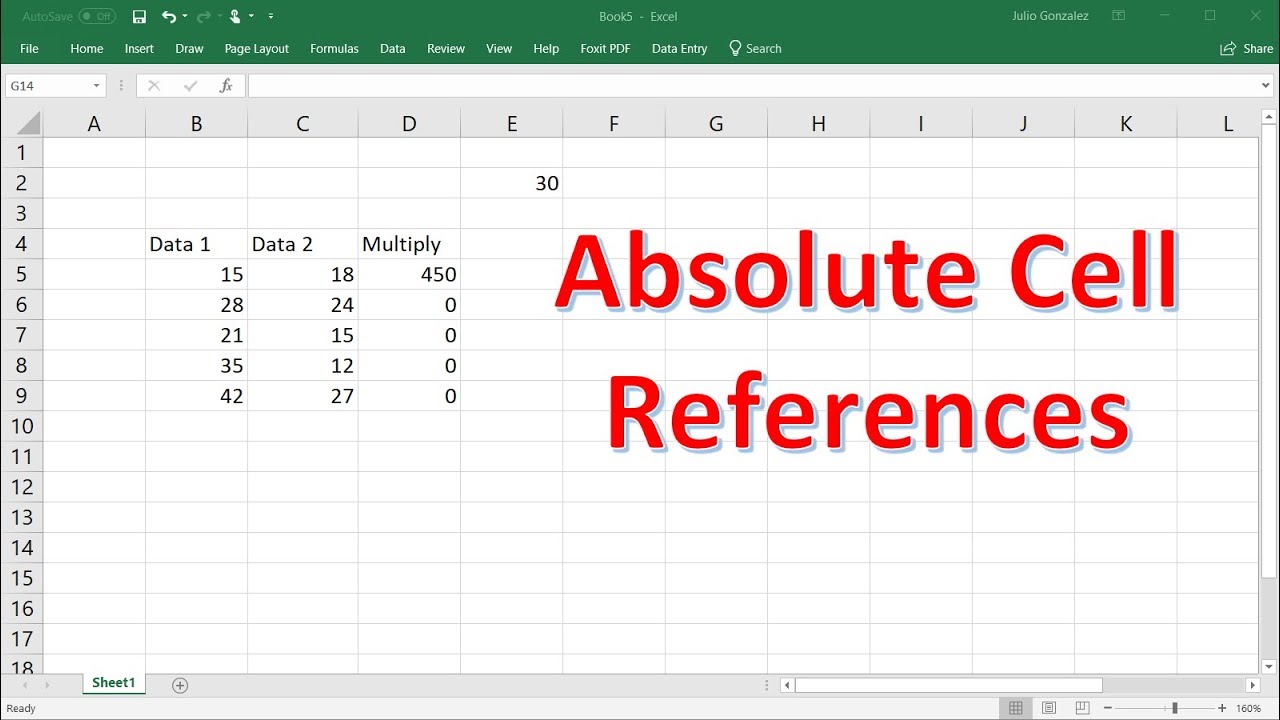
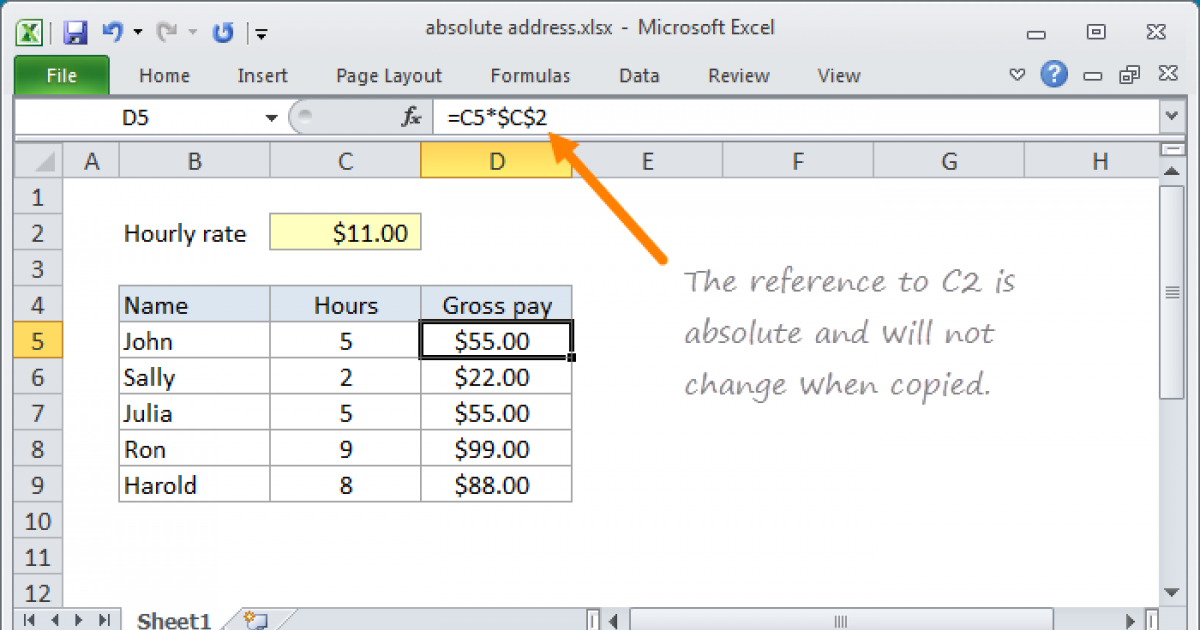
Absolute Reference Excel Formula
Absolute Reference Excel Formula - Remote workforces and byod programs have added layers of complexity to it asset management. Absolute resilience for security™ offers automated endpoint patching and recovery to prevent exploitation and disruption. It combines all the capabilities of absolute visibility™, absolute. It has strengthened our security posture, allowing us to stay in compliance and. Use absolute to prove compliance, reduce asset losses, and drive efficiencies. Today, absolute security users can see all of their devices from a single pane of glass, remotely query and remediate them at scale, and even extend persistence to the rest of their mission. Absolute provides global telephone support in multiple languages so you get the information you need quickly. If you're an absolute partner, log in to our partner portal. Empower your organization to withstand and recover from cyber security threats and attacks on endpoints and installed,. We also provide a customer console that allows you to log in, view devices, and. It combines all the capabilities of absolute visibility™, absolute. Today, absolute security users can see all of their devices from a single pane of glass, remotely query and remediate them at scale, and even extend persistence to the rest of their mission. Absolute secure access packages are offered in three flavors: If you're an absolute partner, log in to our. We also provide a customer console that allows you to log in, view devices, and. If you're an absolute partner, log in to our partner portal. Remote workforces and byod programs have added layers of complexity to it asset management. Absolute core™, absolute edge ™, and absolute enterprise with the included products and capabilities as outlined below. It has strengthened. Today, absolute security users can see all of their devices from a single pane of glass, remotely query and remediate them at scale, and even extend persistence to the rest of their mission. It combines all the capabilities of absolute visibility™, absolute. If you're an absolute customer, log in to the absolute console. Absolute provides global telephone support in multiple. It combines all the capabilities of absolute visibility™, absolute. It combines all the capabilities of absolute visibility™, absolute control™, absolute resilience™ and absolute resilience for security™ with two additional critical features, remediate and. Today, absolute security users can see all of their devices from a single pane of glass, remotely query and remediate them at scale, and even extend persistence. If you're an absolute customer, log in to the absolute console. Absolute secure access packages are offered in three flavors: Absolute core™, absolute edge ™, and absolute enterprise with the included products and capabilities as outlined below. It combines all the capabilities of absolute visibility™, absolute control™, absolute resilience™ and absolute resilience for security™ with two additional critical features, remediate. As a cio, absolute secure endpoint gives me peace of mind. It combines all the capabilities of absolute visibility™, absolute. If you're an absolute partner, log in to our partner portal. Empower your organization to withstand and recover from cyber security threats and attacks on endpoints and installed,. “i can sleep at night because of absolute security. Today, absolute security users can see all of their devices from a single pane of glass, remotely query and remediate them at scale, and even extend persistence to the rest of their mission. Absolute resilience for security™ offers automated endpoint patching and recovery to prevent exploitation and disruption. It has strengthened our security posture, allowing us to stay in compliance. Absolute core™, absolute edge ™, and absolute enterprise with the included products and capabilities as outlined below. It has strengthened our security posture, allowing us to stay in compliance and. If you're an absolute partner, log in to our partner portal. If you're an absolute customer, log in to the absolute console. Today, absolute security users can see all of. “i can sleep at night because of absolute security. Absolute core™, absolute edge ™, and absolute enterprise with the included products and capabilities as outlined below. Empower your organization to withstand and recover from cyber security threats and attacks on endpoints and installed,. It combines all the capabilities of absolute visibility™, absolute. As a cio, absolute secure endpoint gives me. Absolute core™, absolute edge ™, and absolute enterprise with the included products and capabilities as outlined below. It combines all the capabilities of absolute visibility™, absolute control™, absolute resilience™ and absolute resilience for security™ with two additional critical features, remediate and. It has strengthened our security posture, allowing us to stay in compliance and. Use absolute to prove compliance, reduce.How To Calculate Absolute Cell Reference In Excel Printable Online
Excel absolute reference (how to make and use) YouTube
How to Use Absolute Cell Reference in Excel
How To Use Absolute Reference And Relative Reference In Excel Office
Absolute Cell Reference Read A Topic Today
Excel Absolute reference Exceljet
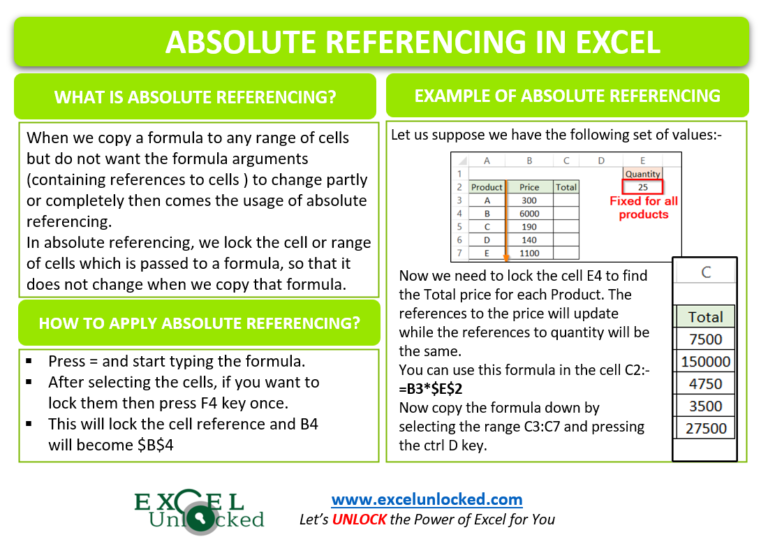
Absolute Referencing in Excel Usage with Examples Excel Unlocked
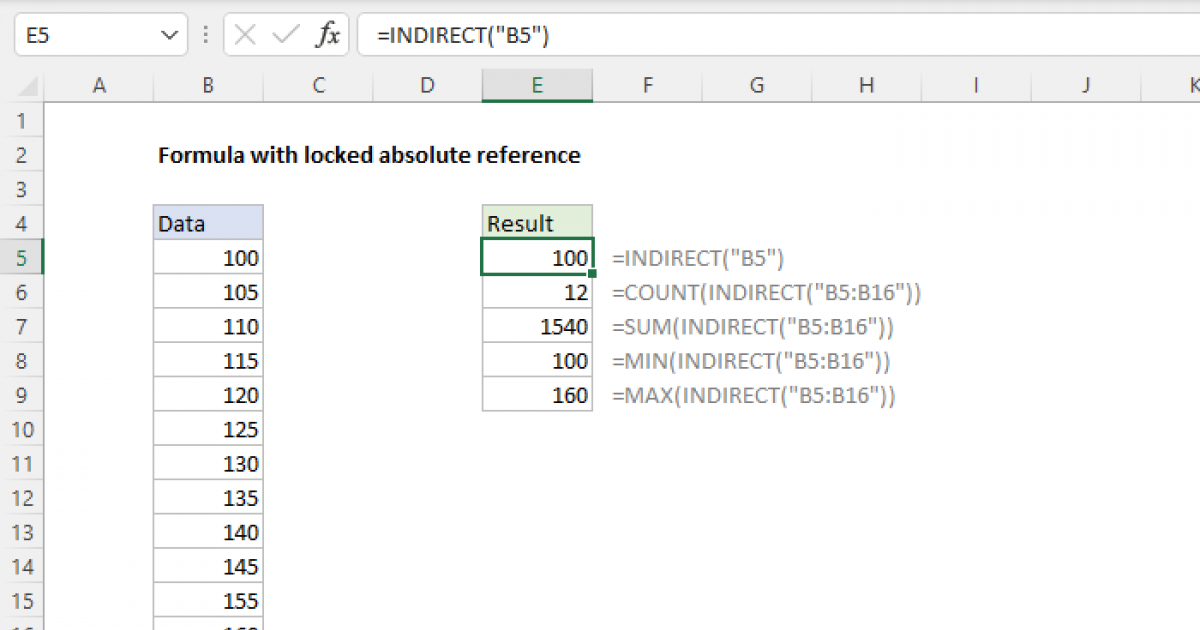
Formula with locked absolute reference Excel formula Exceljet
How To Use Absolute Reference And Relative Reference In Excel Office
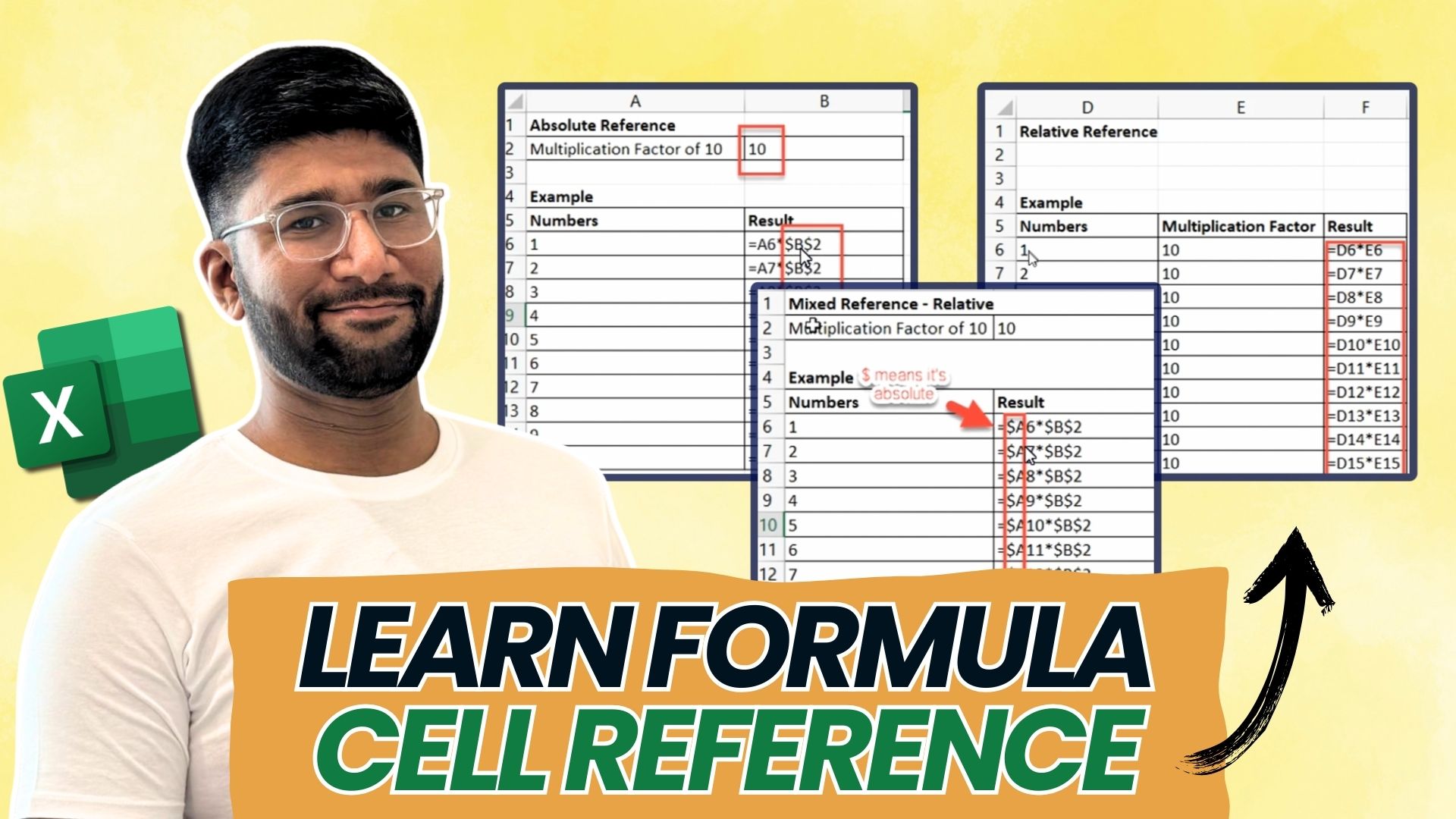
How to Make Absolute Reference in Excel Earn & Excel
Related Post: